
ROUND ROCK, TX – A security incident has come to light, prompting concerns among users. Dell Technologies, a prominent player in the tech industry, disclosed a data breach affecting a substantial number of customers, totaling 49 million.
While the breach does not involve sensitive financial or payment data, it nonetheless exposes personal information, including full names, cities, postal codes, and purchase details. Despite seeming innocuous, this data can be exploited by cybercriminals to construct comprehensive profiles, potentially leading to identity theft or susceptibility to scams.
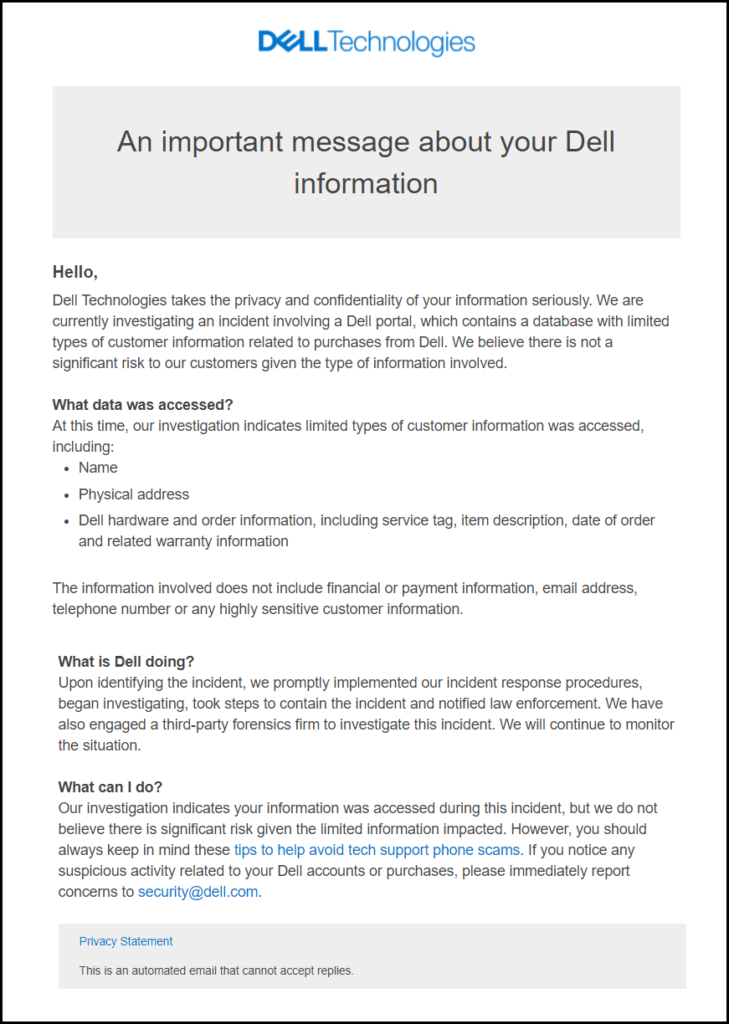
In response to this breach, Dell Technologies urges all customers to prioritize their digital security.
Here are some essential steps you can take to safeguard yourself:
- Stay Updated: Regularly update software and applications on all your devices. These updates often contain crucial security patches that address vulnerabilities exploited by cyber threats.
- Password Hygiene: Practice good password hygiene by creating strong, unique passwords for each online account. Change passwords regularly and avoid using easily guessable information.
- Beware of Phishing: Exercise caution when dealing with unsolicited emails, messages, or calls requesting personal or financial information. Phishing attempts often disguise themselves as legitimate communications, aiming to trick users into divulging sensitive data.
The repercussions of a data breach extend beyond the initial exposure. Even seemingly insignificant information can be pieced together by malicious actors to orchestrate sophisticated attacks. By remaining vigilant and implementing robust security practices, individuals can mitigate the risks associated with such incidents.

About The Author: John Colascione is Chief Executive Officer of SEARCHEN NETWORKS®. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a how-to book called ”Mastering Your Website‘, and is a key player in several online businesses.

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
Leave a Reply