PALM BEACH, FL – Sometimes I read stories that really make me think (and worry). For those who have great domains under management, you might feel super-safe by using “two factor authentications”, where your mobile device is used to verify each login you make to your registry account by sending you a text message for confirmation.
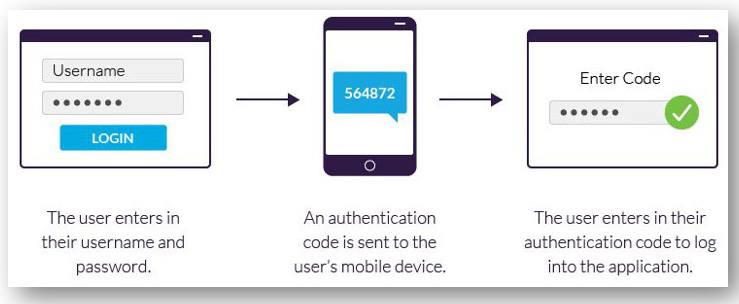
I’ve often thought how horrible it might be if someone got control of my mobile device and was able to use it to verify an account change such as a password update or confirmation for logging in. The same goes for your bank accounts. What if someone could somehow intercept your text messages?
In most cases your cash in bank accounts is protected by Federal Deposit Insurance Corporation (FDIC) [Banks] or the National Credit Union Insurance Fund (NCUSIF) [Credit Unions].
Who is insuring your domains?
The experience of such a device takeover is what happened to Seth Shapiro, who happens to be a technology consultant that advises businesses on such things as digital innovation and strategy.
Shapiro is suing wireless service giant AT&T (Seth Shapiro v, AT&T Mobility, LLC) for allegedly (and maliciously) transferring his cell phone service to another device by facilitating a SIM card swap where Shapiro lost $1.8 million, some of which was in the form of digital coins or cryptocurrency.
The suit alleges:
On at least four occasions between May 16, 2018 and May 18, 2019, AT&T employees obtained unauthorized access to Mr. Shapiro’s AT&T wireless account, viewed his confidential and proprietary personal information, and transferred control over Mr. Shapiro’s AT&T wireless number from Mr. Shapiro’s phone to a phone controlled by third-party hackers in exchange for money.
The suit also alleges that not only was AT&T responsible for his loss, but that his account compromise was maliciously carried out by the carriers’ employees who were allegedly in on the heist based on information obtained from chat messages:
At the end of the chat, a group member brags that they “made 1.3 [million]” and they begin plotting about how to route the stolen cryptocurrency through various accounts and currencies in order to cover their trail. They also brag about plans to “buy some Gucci” or a “dream car” with the money they stole from Mr. Shapiro.
Shapiro is not the only victim who uses AT&T that has experienced this “digital identity theft” method known as “SIM swapping,” where criminals steal phone numbers to log into accounts.
Back in July of this year AT&T failed to win a dismissal in a $24 million SIM-Swap lawsuit brought by Michael Terpin (Terpin v AT&T Mobility) when a judge decided the suit could move forward. Recently Terpin wrote an open letter to the the FCC Chairman laying out the need for additional oversight and regulation with more than 50 victims of SIM swapping.
I am not alone, of course. The REACT Task Force has taken on hundreds of cases (including new ones every month I refer to them; since I announced my lawsuit, I have been contacted by more than 50 individuals who experienced similar hacks, with losses in a few instances of more than $10 million).
The letter recommended the following actions:
- Mandate that all US mobile carriers cover their PINS and passwords, so that users must punch them in instead of reading them aloud to a retail clerk or call center employee. Banks, hotel chains and airlines cover their passwords. The vital data and access protected by these four- to six-digit PINS is too valuable to trust the screening out of potential criminals from tens of thousands of employees and agents. Let the technology do the work and protect all consumers.
- Inform all US mobile carrier customers that they can opt-in to carrier high-security plans (all carriers have these, but they don’t inform customers at the time of purchase, as they do with insurance against damaged devices). These high-security plans must include a “no port” option, whereby a consumer can specify that his phone cannot be ported without going through the fraud department. This would be similar to how credit card companies protect their consumers.

About The Author: John Colascione is Chief Executive Officer of Internet Marketing Services Inc. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a ‘how to’ book called ”Mastering Your Website‘, and is a key player in several Internet related businesses through his search engine strategy brand Searchen Networks®

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
This is why you shouldn’t use SMS-based two-factor. Use app-based or physical security key.
Vulnerabilities in the SS7 network and sim swap attacks alone can not account for the increase in ATO for accounts that require password + OTP/SMS to Sign-In.
OTP is defeated by Man-in-the-Middle, social engineering, malware, & phishing, if the bad actor is able to intercept the credentials (password and OTP) that the user is attempting to communicate to the authentication service. If the bad actor knows the OTP, even if they don’t have the phone (or SIM card), they can pass the OTP challenge.
With this understanding, the OTP is more correctly thought of as a dynamic knowledge factor than a possession factor. Knowledge + knowledge should not be considered MFA, 2FA etc.
Said plainly, OTP from an app (TOTP) or physical token is just as vulnerable to social engineering, phishing, MitM, etc as OTP/SMS.
Certificate based authentication protected with a local biometric or local pin code is a much stronger authentication method. Thankfully WebAuthN is now an official standard. By this time next year I expect many more sites to reduce reliance on Passwords and One Time Passwords, and replace them with WebAuthN.