Below is why you should get ‘out of the habit’ of clicking on any links within an email. Scams are running rampant with email and they’re not always easy to spot with the naked eye, so be cautious and think before you click.
PLEASE NOTE: THE PHOTO EMAIL BELOW IS NOT SENT FROM VERIZON®. IF YOU RECEIVE IT, IT’S A FAKE. IT IS BEING USED BELOW AS AN EXAMPLE OF AN ACTUAL “PHISHING” EMAIL I RECEIVED. VERIZON® IS ALREADY AWARE OF IT AND TRYING TO PUT A STOP TO IT. THIS IS HERE TO HELP OTHERS AVOID IT AND EMAILS LIKE IT AS WELL AS TO ILLUSTRATE HOW THE SCAM WORKS IN DETAIL.
Today I received a fake but cleverly designed Verizon Wireless “phishing scam” email in my inbox. The subject line is the usual “Your Bill Is Now Available“. I’ve been getting this for what feels like so many years now, but once in a while I see one that still almost gets me. Lucky I was too busy to even think about it much at the time, click any links or look into it at all so I figured I would get back to later. It indicated that I had an astronomically high monthly usage bill of $1,760.76.
The email says:
Your current bill for your account is now available online in My Verizon
Total Balance Due: $1760.76
Keep in mind that payments and/or adjustments made to your account after your bill was generated will not be reflected in the amount shown above.
> View and Pay Your Bill
Want to simplify payments?
> Enroll in Auto Pay
Thank you for choosing Verizon Wireless.
I knew something couldn’t be right. I checked into it later and noticed that is was addressed to the wrong email, which is what first tipped me off that it was fake. I haven’t written anything on these for a very long time, but these scams have been going on for a long time and are nothing new, they are just becoming more wide spread and sophisticated.
I’ve already gotten into the habit of not clicking on links in my email so I didn’t even click the links there, but this is a pretty clever scam email because I can see how it would easily fool so many unsuspecting people. Hundreds of thousands of people have likely opened these up over the last few months. I called Verizon about it and they do know about it, and explained that they are already working on tracking it down. A search for ‘Fake Verizon Wireless Email” also returns a lot of results on Google.
Below is how good they made this one look:
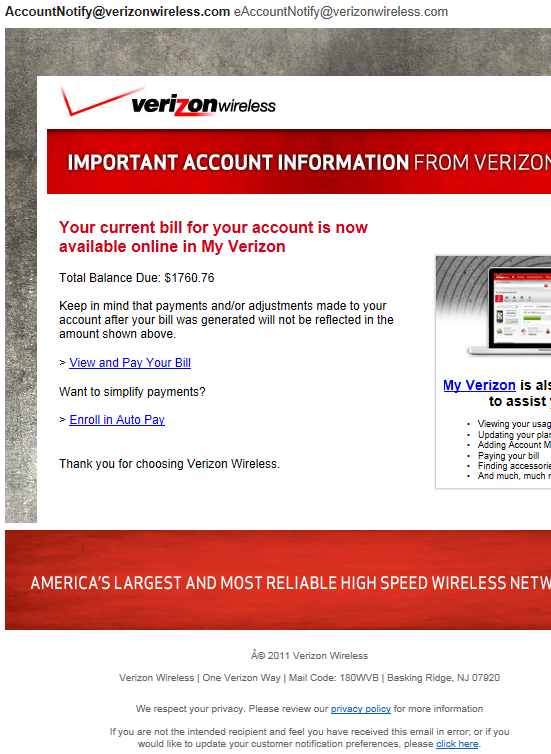
This email did not actually originate from the email address which appears as the sender at the top of the email. It did not come from AccountNotify@verizonwireless.com or eAccountNotify@verizonwireless.com. This is called email spoofing. The email actually comes from the IP Address 196.20.167.242 which translates to Mauritius, officially the Republic of Mauritius, a small country on an island off the southeast coast of the Africa. The links also do not go to Verizon either. No, they go somewhere far more malicious.
Here is what is really behind this email:
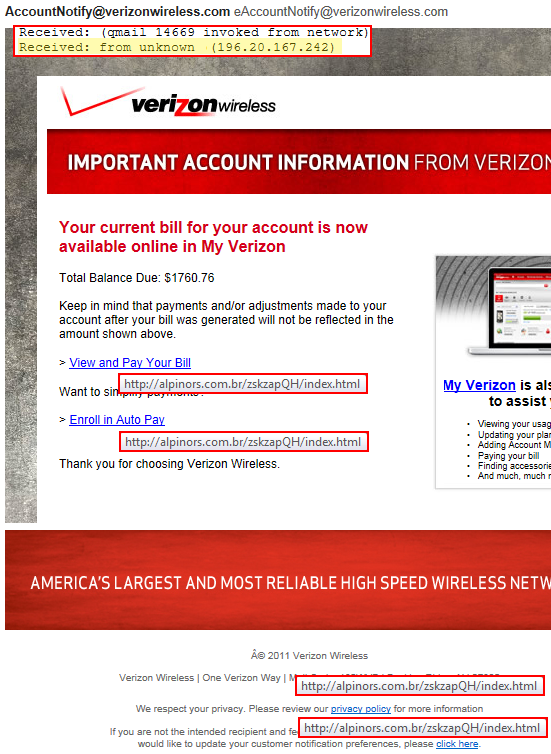
The IP Address is found within the headers of the email. Different email programs work different ways, but they usually have an option to ‘show original’, ‘view source’ or ‘view email headers’. This is where you can see all the intricate details behind the email, such as where it came from. Again, for this particular email the IP Address 196.20.167.242 is from Mauritius. This means whoever sent the email either sent it from there, or they remotely connected to a computer (possibly compromised, broken into or hacked) and send this email from a machine (server) which is located in Mauritius. Now that doesn’t mean that’s where the person is behind this email, but it does mean they had a connection to a computer server over there in order to send this mail. This is what makes these hackers and scammers so difficult to catch.
Tracing the IP Address returns the following info about its location and origin (where the mail server is):
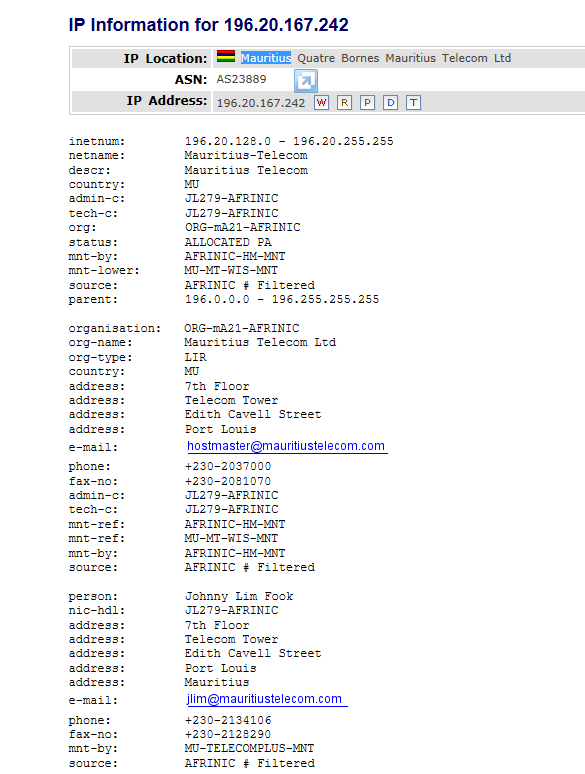
The web site address is actually tracing back a Brazil TLD .bz and is hosted in Brazil:
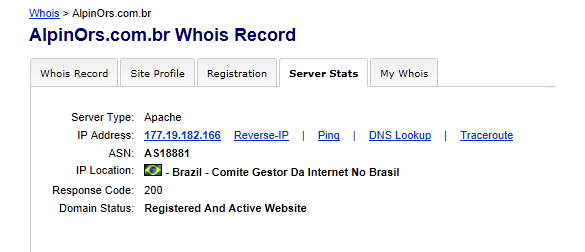
The sites IP (not the mail server but the site IP of 177.19.182.166) traces back to Brazil and a domain name registrar in Brazil with the following Whois record:
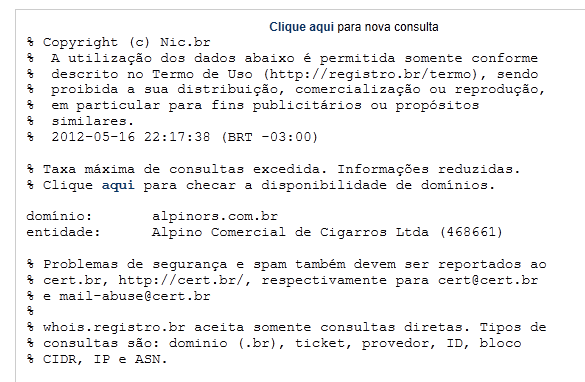
The following WhoIs Record translated in English to:
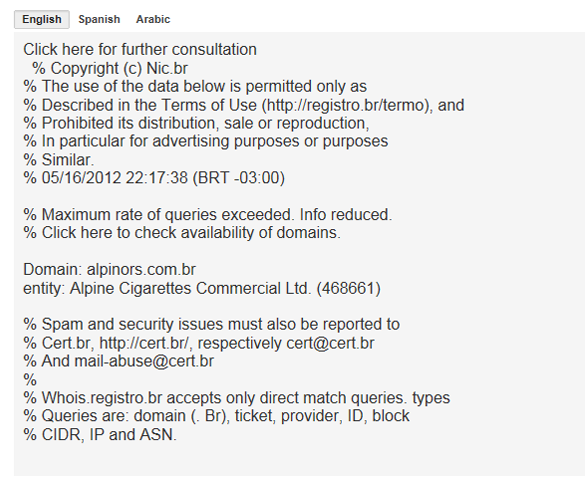
So What’s This All About? What’s Their Overall Goal?
There are many different reasons why these spammers do this type of stuff, but it is usually to take advantage of you or scam you in some way, shape or form. It’s always about them making money somehow, by either:
- Making you visit a malicious site to install a virus on your machine.
- Take over your browser to serve you with ads.
- Take over your computer and log your keystrokes.
- Use your computer as a host to send email or spam (probably what happened here in Mauritius)
- Have you visit a fake (authentic looking) page and log-in, at which point they steal your passwords.
- Or just snoop, steal from, or otherwise cause harm to you or someone else.
I was really curious to click on these links just to see what is going on at that URL in the email alpinors.com.br/zskzapQH/index.html (Don’t try it), but I know better, so what I’ll do first is a Server Header Check on the URL to see if it redirects me somewhere else, but it doesn’t. It returns a status 200, which means OK – the page is there.
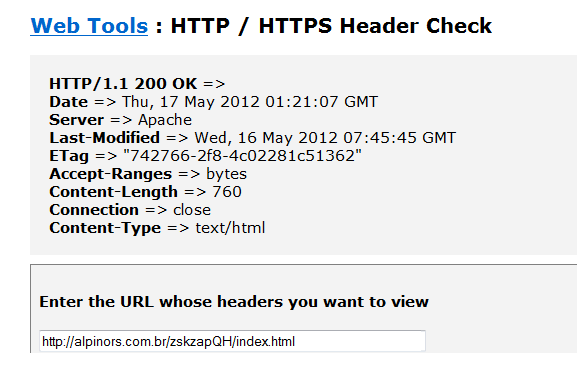
So now that I know what is there I want to look at the source code which is hidden behind the web page. I can do this with a Source Code Viewer.
There It Is! (The Goal) – To Get You Here (below) So Whatever That Mess Does Gets You:
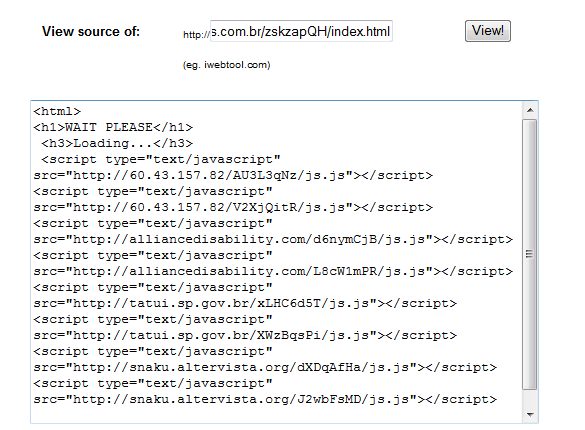
Looks like when the page loads it is going to quickly redirect me to yet an additional location. Looks at these guys go! They’re relentless. Looks like there is a bunch of JavaScript waiting to load on that page:
- two from 60.43.157.82 (Japan Tokyo Open Computer Network)
- two from alliancedisability.com 173.201.92.1 (hosted at GoDaddy, probably don’t even know they’ve been compromised)
- two from http://tatui.sp.gov.br (200.144.6.216, Brazil – Comite Gestor Da Internet No Brasil)
- two from http://snaku.altervista.org (108.162.207.65, California – San Francisco – Cloudflare Inc, another machine likely compromised).
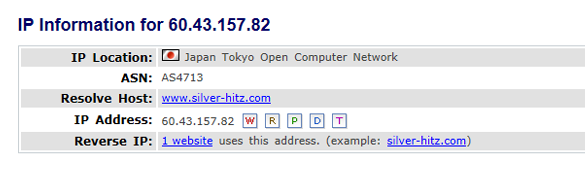
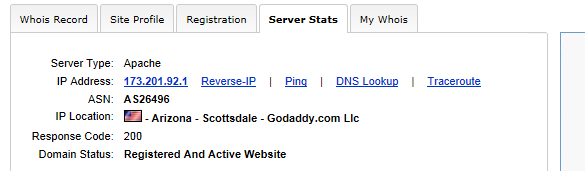
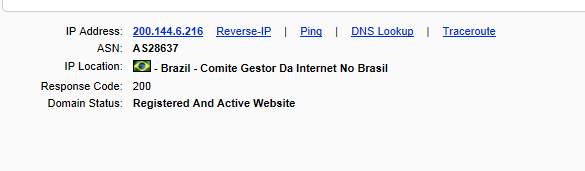
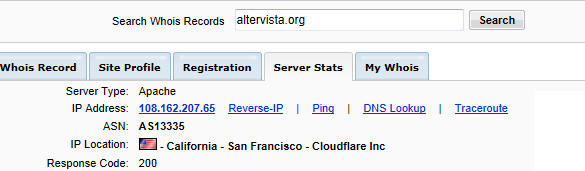
There is a very good possibility that each one of those sites which hosts that script is actually doing the same thing. The reason there is four of them is so that if any one of the four sites (which have been hacked and used to run these scripts for visitors) finds out the scripts are there and removes them, there are 3 back up sites still being used, so that the entire plan does not get compromised from one site owner realizing he has been hacked and removing those scripts. In order for the email blast scam to fail, ALL four web sites would need to realize they have been hit and remove the scripts at which point the entire plot is foiled. Anyone who clicks on the links in the email will get a page that does nothing and the whole thing is over, at which point, the scammers go find more machines to hack, more malicious scripts to install, more machines to take over and send spam from, and the entire thing starts over again.
It’s very difficult to catch these scammers because by the time you get to them they’re usually gone and have moved on to other machines to run their scam.
I called Verizon Wireless and spoke to someone about this to make sure they were aware of it and they are. There was also no need to send it in or forward it over as they have received many reports of the incident already, and are investigating it to the best of their ability. This is a very difficult task for them to prevent, so they are working hard to ensure customers are aware of it.
SO IT IS VERY IMPORTANT TO:
- Never Log-in to any financial web sites from an email.
- Always check if you are visiting the actual URL by looking in the address bar.
- If visiting a financial site or your ready to make a purchase online, look for the https:// – “green bar” and lock, most reputable sites have it.
- Always hover over a link and view the task bar to see it’s address and double check that the page loads the correct site URL.
*** UPDATE: ON APRIL 20th, 2013, I ADDED PART 2 WHICH DETAILS AN ADDITIONAL EMAILS USING VERIZON: http://www.strategicrevenue.com/fake-verizon-wireless-email-email-scams-how-to-avoid-them-part-2/
For more information on this as well as what to do about it visit:
- http://support.verizonwireless.com/how_to_use/fraud_email.html
- http://www.longislandexchange.com/identity-theft.html
- http://www.ftc.gov/bcp/edu/pubs/consumer/alerts/alt127.shtm

About The Author: John Colascione is Chief Executive Officer of Internet Marketing Services Inc. He specializes in Website Monetization, is a Google AdWords Certified Professional, authored a ‘how to’ book called ”Mastering Your Website‘, and is a key player in several Internet related businesses through his search engine strategy brand Searchen Networks®

 *** Here Is A List Of Some Of The Best Domain Name Resources Available ***
*** Here Is A List Of Some Of The Best Domain Name Resources Available ***
Leave a Reply